What is encryption?
How does encryption work?
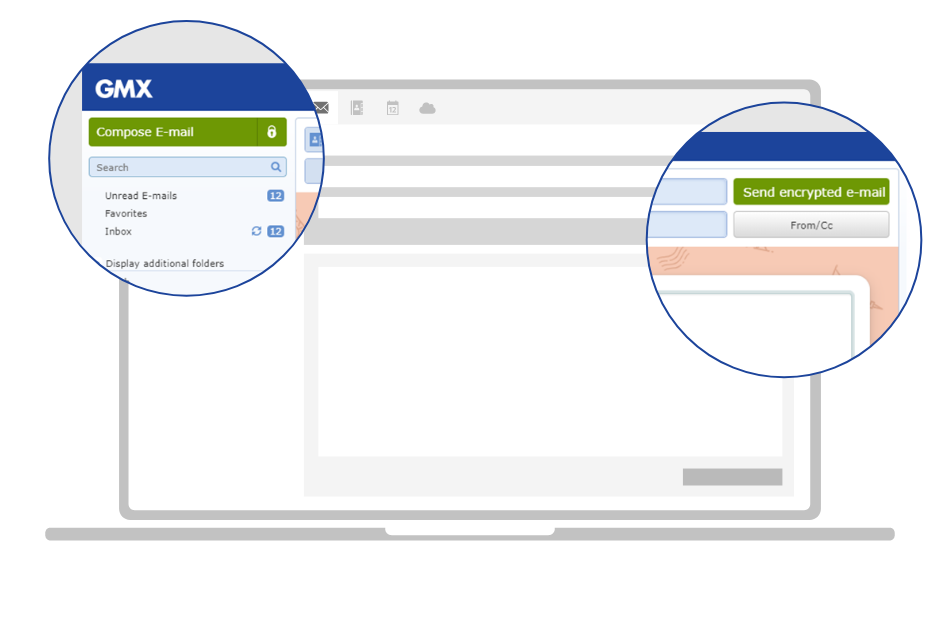
Encrypt your emails in 3 steps
It’s that easy!
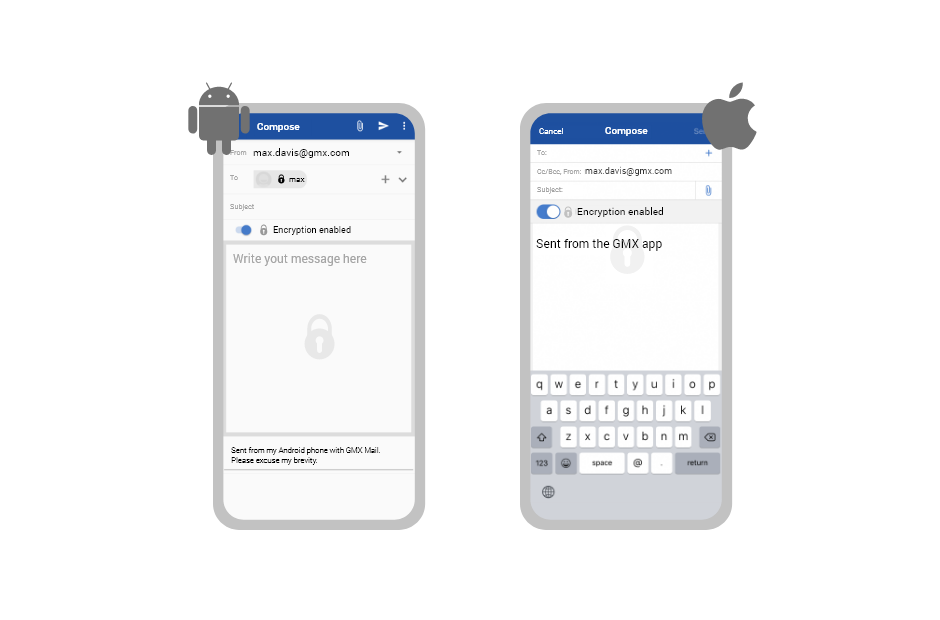
Encrypted emails
Write encrypted emails the way you normally would!
Encryption details
Easy & safe to use
Encryption gold standard
Information & details
Encryption gold standard
Emails are encrypted using OpenPGP (from Pretty Good Privacy), the open source gold standard for secure and speedy end-to-end encryption of email content. OpenPGP has not been cracked since its introduction, meaning it is considered completely secure. Encrypted communication provides the greatest level of security and makes the sender, recipient, subject (metadata) and content inaccessible to unauthorized parties.
The OpenPGP process
PGP email encryption uses two interdependent keys for encryption and decryption – one public and one private. The public key is sent to the communication partner, ‘locking‘ their message so that only the person with the private key can decrypt it – which is why the private key should remain secret. This principle of complementary keys ensures the highest level of security.
Worldwide use
OpenPGP email is a globally recognized encryption procedure and is therefore ideal for encrypted communication across countries and systems. Other encryption processes only offer one-way communication within the respective encryption program and are often not transparent in terms of security and functionality. OpenPGP, on the other hand, has made its procedure and functionality known in a comprehensive manner.
Easy to use
Information & details
Easy to use
GMX aims to provide unhackable email communication to users without requiring them to have expert knowledge. Thanks to email encryption, this is now possible. GMX has optimized the OpenPGP procedure to make it user-friendly. This was achieved in cooperation with the Mailvelope open source project from Heidelberg, Germany, which offers its own browser-based OpenPGP solution.
Easier key generation
The 3-step setup process simplifies the usually lengthy key-creation process. During setup, the pair of keys required for encryption (the public and private keys) are created in the background so that the user does not have to be concerned with the technical process. The local storage of the keys in the browser extension ensures that access from outside is not possible. The key password created during the setup provides an additional layer of security to the encrypted email communication. Users who already have a PGP key pair can import it via the options in the extension.
Optional backup
Users can set up a backup in the third step of the setup process, which allows the user to recover a lost key or key password. Encrypted messages can no longer be decrypted if the key or key password was lost without a backup. Mailvelope encrypts the required data in a security container and secures it with a 26-digit code. This recovery code is not stored, but only put out via a document to be printed by the user and then stored securely. Although the backup is optional, it is highly recommended.
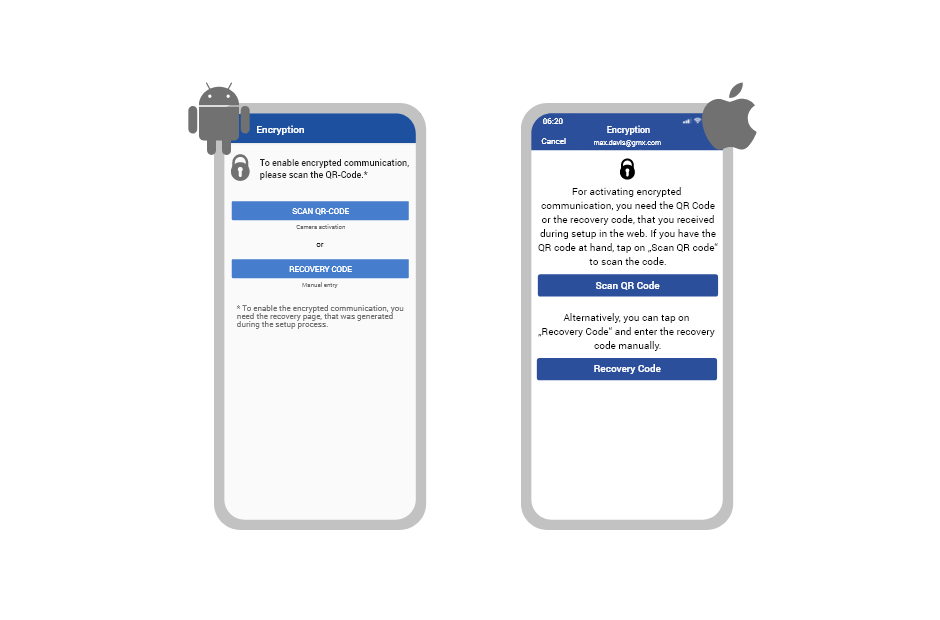
Mobile use
Using email encryption on mobile devices is yet another innovation GMX provides when compared with existing OpenPGP procedures: using a QR scan or the recovery code from the document created during the backup setup, users can activate email encryption in their mail app. After successfully setting up encrypted communication on the PC, the mail app automatically offers the option to transfer this capability to mobile devices.
Improved key management
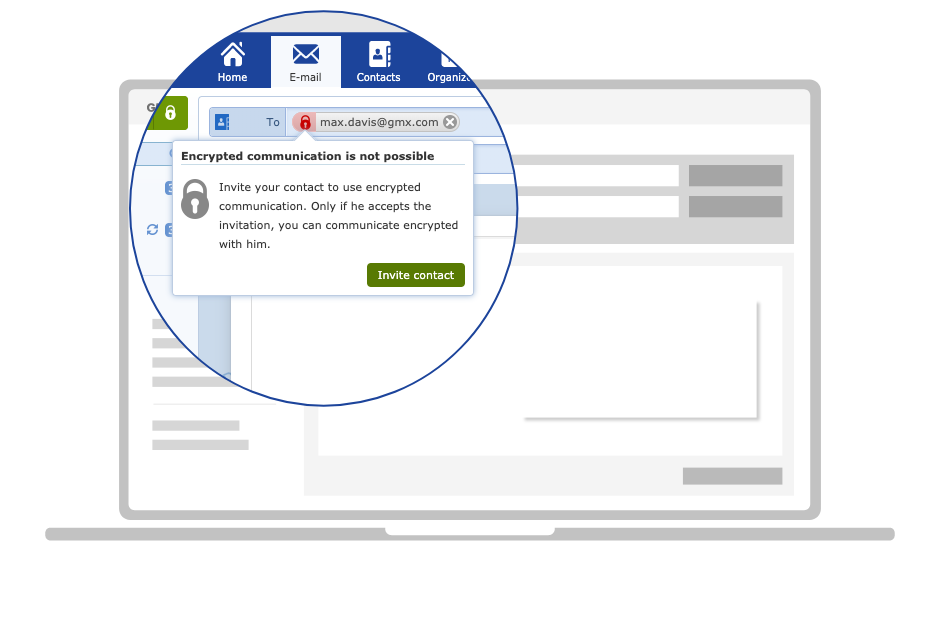
Encrypted communication requires that both the sender and recipient have the public key of the communication partner. Normally, this would require keys to be exchanged and verified manually. GMX provides two easy alternatives to this manual process.
If the recipient of the encrypted email has not yet set up encryption, the sender must first send a personal invitation via email, which will provide the recipient with both the public key of the other party and the chance to start setting up encrypted communication. Once the recipient has completed the setup, their public key will be sent to the sender in the background.
If the recipient has already set up encrypted email communication, their public key will already be in the GMX key directory. If the sender enters the recipient’s address, the public key is automatically made available to them. All stored keys carry the GMX signature, which guarantees authenticity. If storing the public key is not desired, it can be removed from the GMX key directory at any time via the mailbox settings.
Verified security
Information & details
Verified security
By disclosing how the process works and the source code behind it, GMX encryption is made transparent. It is also audited by external security experts. All this guarantees the security of the procedure – even with better usability.
Browser-based method
Because only browser-based encryption enables true end-to-end encryption, GMX has deliberately opted for this type of procedure. Encryption takes place directly on the user’s computer and not on the provider’s end. The partnership with Mailvelope has also ensured that encryption technology and user data always remain separate.
Other security settings
The Mailvelope browser extension offers further security options. The graphical security background, displayed during all stages of encrypted communication, can be individually customized. This allows users to check to make sure the window has not been manipulated. Another security feature is Mailvelope’s security protocol, which can be viewed via the settings. This logs all of the user’s actions with the browser extension. The 'OK' displayed in the browser extension informs the user when they are accessing the extension via the security window.
Encryption – Questions & Answers
The 5 most frequently asked questions about the procedure
How much does GMX encrypted communication or the Mailvelope browser extension cost?
GMX’s encrypted email services are provided free of charge.
I need help with the setup. Is there a manual?
You can find detailed step-by-step instructions for setting up encrypted communication here.
How secure is encrypted communication?
GMX encrypted communication uses OpenPGP (from Pretty Good Privacy) for its encryption, an encryption process that has not been cracked since its introduction. This encryption can therefore be considered very secure.
How do I compose a new encrypted email?
Write a new encrypted email the way you normally would using your mailbox. You will find a button with a lock next to the “Compose Email” button, which you should click on to compose an encrypted email. For detailed instructions, you can also visit our help page about sending encrypted email.
What happens if I have lost my key or forgotten my password?
GMX offers the option of setting up a backup with a recovery document. The recovery document will have a recovery code printed on it, which you will use to recover your password and key. It is therefore especially important that the recovery document is kept safe from and untraceable for unauthorized individuals.
Further security questions
Everything important spelled out in detail
Are email attachments also encrypted?
Yes, email attachments like pictures and other files are also encrypted with OpenPGP.
What does the Mailvelope browser extension do with my data?
Mailvelope creates and manages the keys and stores them locally in the device’s browser extension. Access from outside the computer is not possible.
Do providers or government agencies have access to my emails?
No. Browser-based storage means that all important data is stored by the user. Neither government agencies, nor GMX, nor Mailvelope have access to the encrypted email content. Even court decisions on data delivery will remain ineffective because of this.
Are my emails always readable for others once they have been decrypted?
No. Decryption only makes the content temporarily and locally visible on a device, and must take place every time the email is opened.
What is the difference between SSL encryption (Secure Sockets Layer encryption) and email made in Europe?
Encrypted communication complements transport encryption and offers protection even if the email leaves the secure email made within the European network. Even if emails are sent abroad, and to email providers with weaker data protection regulations and without encrypted connection paths, complete data protection can be ensured because only the authorized recipient will be able to decrypt the message.
Why do we use browser-based storage?
Browser-based encryption ensures that the encryption takes place locally on the user’s computer and not in the provider’s infrastructure, unlike the server-side method. The cooperation with Mailvelope also ensures that all security-relevant data such as keys or associated passwords are outside GMX’s sphere of influence. This guarantees the separation of encryption technology and user data.
Why did we choose OpenPGP for encrypted communication?
OpenPGP is an encryption standard used worldwide that is compatible with different systems and provides the highest level of security. Transparency and long-term security are ensured through the disclosure of the source code and functionality of encrypted communication, as well as through monitoring by external security service providers.
Was there a review of the encryption process?
Yes, the encrypted email process was checked by external security service providers.
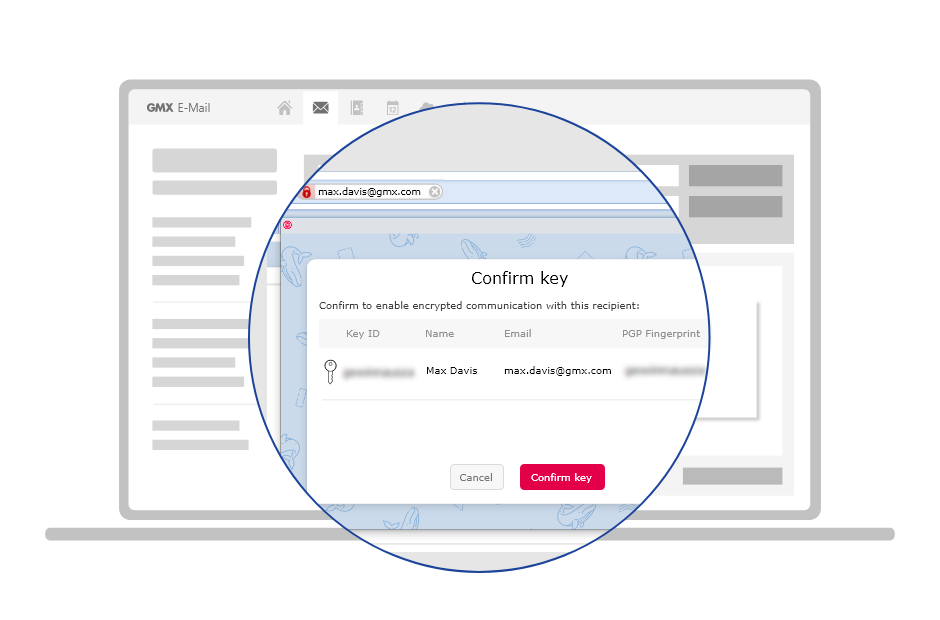
How can I check whether a key actually belongs to the specified sender?
Use the PGP check number (or ‘fingerprint‘) to be sure that a key actually belongs to the specified sender. When you confirm a new contact for encrypted communication, an 'i' will appear next to their email address. Clicking on the 'i' will display your contact’s fingerprint. To make sure that it actually belongs to the specified sender, have your contact confirm it in person or over the phone.
How can I tell if the key has been signed by GMX?
GMX signs all keys stored in the key directory with its public key to guarantee their authenticity. To check whether a key has been signed by GMX, import the GMX key in the Mailvelope browser extension options. The corresponding fingerprint is: C394 C011 0A17 0954 47F1 5F0D 1DA4 1713 9553.
What does the digital signature mean?
All encrypted messages are digitally signed by the sender by default. The signature states that the email originates from the specified sender and that the content has not been manipulated during transmission. You can check whether a signature is valid in the lower left-hand area of an encrypted email.
Further setup questions
Everything important spelled out in detail
Do I have to set up the encrypted communication at GMX every time I wish to send an encrypted email?
No, each user only needs to set up the email encryption service once.
Is encrypted communication mandatory?
No, the setup of encrypted communication is voluntary. Even after setup, you always have the option to encrypt the email content or not.
I have forgotten my password and lost my recovery document. Can I re-establish the encrypted communication?
If you have lost both your password and your recovery document, our customer service can reset encrypted communication for you. However, the emails sent and received up to that point cannot be decrypted.
Can the key password be changed?
No, the key password cannot be changed, nor can it be reassigned. You can display it, however, using the recovery code if you have forgotten it.
I’ve already created keys. Can I import them?
Yes, you can import your keys using the expert settings in the Mailvelope browser extension. Please note, however, that these imported keys are not synchronized and cannot be recovered via the recovery document. The keys created by Mailvelope and GMX should also not be deleted. Otherwise, the setup of the GMX encrypted communication will no longer be recognized.
How can I set up encrypted communication if I already use Mailvelope?
For instructions on how to migrate your keys, please visit our help page about managing keys with Mailvelope.
Can I also decrypt emails that I have previously encrypted via the mailbox?
Yes. To do so, import the key pair for the already encrypted emails via the expert settings in the Malvelope browser extension and forward the emails to your mailbox. Note that these keys are not synchronized and cannot be recovered via the recovery document. Do not delete the keys created by Mailvelope in cooperation with GMX. Otherwise, the setup of encrypted communication will no longer be recognized.
How can I deactivate encrypted communication?
If you no longer wish to be able to use encrypted communication, our customer service can reset your account. Note, however, that already encrypted emails can then no longer be decrypted.
Further usage questions
Everything important spelled out in detail
Can I also communicate with other email providers in encrypted form?
Yes, encrypted communication is also possible with other email providers, as long as they also use OpenPGP.
Where can I find my encrypted emails?
Encrypted emails that you have received can be found as usual in your mailbox – encrypted emails sent by you can be found in the 'Sent' folder. Encrypted emails are marked with a lock icon for easy differentiation.
How can I tell if my communication is encrypted?
You will be able to tell if you’re reading or writing an encrypted email thanks to its colorful background. This background can be customized to make it your own. The 'OK' displayed in the browser extension indicates when you are accessing the extension via the security window. For more information, please visit our help page about receiving and reading encrypted email.
Can I copy the content of a decrypted email (Ctrl+C)?
Yes, this is possible with no problem. However, please note that copied content is decrypted in the cache. The decrypted content can therefore still be retrieved after having logged out if the cache has not been emptied or overwritten.
Can I read encrypted emails even if I have forwarded my GMX mailbox to another email address?
Yes, as long as encrypted communication has been set up with the destination mailbox. If the target mailbox is an email provider other than GMX, the encrypted communication may not be offered or the setup process may be more complicated.
What is the Key Directory?
After setup, your public key is stored by default in the GMX Key Directory to simplify communication. When you enter your recipient address, this is automatically detected and your public key is made available to the sender. If you do not want your keys to be stored in the Key Directory, you can revoke your consent in the mailbox 'Settings' under 'Encryption' > 'Privacy'.